However on Saturday, this all changed. My Twitter mentions feed was all in Thai and my DMs were filled with people asking for their data and what they should do.
Q. Did you hack the site?
No. I found the location. It was a lucky guess is the best way of describing it.
Q. True Corp are saying it is a hack?
It is a data leak. There was no security on the S3 bucket with the data. Google could have indexed it as well as any other search engine. If you found it, it was the same as browsing to a website.
Q. Did you download all of the data that was publicly accessible?
No. I selected 4 files at random to verify the contents of the bucket. Past those initial files that confirmed that this bucket was holding sensitive data, I did not download any other files. At this point, I notified True Corp of the issue.
Q. Have you a copy of my data?
No. I have deleted all files related to this disclosure
Q. Can you help me find if my data was in the leak?
No. I do not have a copy of the data nor can I check if your data was in the leak. You can however ask True Corp to verify that your data was not in that particular location
Q. What did you do once you found the files?
I notified True Corp support as detailed in my original post
Q. How many files were involved?
45736 files which were a mix of JPG and PDF files.
Q. How did you find out there were so many files?
I used a tool called s3-ncdu to generate a list of all of the files and file sizes in the bucket. This showed the folder structure and approximate files sizes.
Q. How long was the data available?
For at least from when I found it and until the 12-April-2018. It could have been available before that as well.
Q. Could someone else have found it other than you?
Yes. If I found it, someone else could have done so
Q. Could someone else have downloaded the data?
Yes. If they wanted to, they could have downloaded the entire bucket.
Q. People are calling you a hacker, is that true?
No. There was no hack here, the files were publicly facing on an unsecured system. This means that anyone could have found them with a careful Google search for example. No tools other than your browser (IE, Chrome, Firefox etc) are needed. What I did was find the issue, alert True Corp to the mistake and push that they fixed it before anyone else could find it and use it.
Q. Why did you wait one month before publishing?
To ensure that people's data was not put at risk by me publishing this information, I had to wait until the files were not available anymore. If I had published while the files were still available, someone else could have found it and used it for bad things.
Q. Why didn't True Corp respond?
When you send in information like this to a company, some are very good and will respond within minutes and fix the issue which is good. Others, take more time or do not have the correct processes in place to handle this type of problem.
Q. What is the risk to my data?
I don't know. I can give information on the technical part of this issue.
Q. What should I do if I am worried my data was in this leak?
Contact True Corp to verify that your data was or was not in the leak. Once you know, you can decide on the correct course of action for you.
Q. How could this happen that the data was not protected?
It could have been a simple oversight due to lack of testing or understanding of the security implications. Someone could have disabled security accidentally or worse someone could have turned it off maliciously which would a more worrying issue.
Q. Where can I find more information
Please see the ThaiCERT page here
Q: Have you been contacted by the company after this?
No. They have not contacted me to ask for clarification on any of the issues.






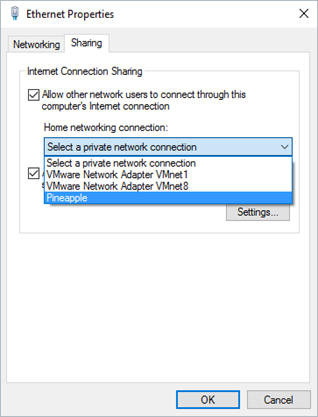




![WP_20160101_14_37_31_Pro_thumb[1] WP_20160101_14_37_31_Pro_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj9Cpvh1JO2KonlKDwnQUPtFsVg3qPbC1jktwLiDXRy2cMcL1T8uYiNCcPdaRrPu20Xgm1Pjz6476_Do2lfGADQsCmZI0zhmJIO6qxerpIF5NCBIZmlm1kE1V1kr2wC9HN2wivr9gIZlw/?imgmax=800)
![WP_20160101_14_37_03_Pro_thumb[2] WP_20160101_14_37_03_Pro_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhG1-6OO2JBfSZAU_hviRKwVdMjXkYtCZlJaxhJWQZY2GonOCMU2OuMXjAFGJIeSgh9X2C_4TL6_Y-A3kArxx7kxR-ymBGnDAZxEntR7isEeCGLThrAJI8UFqLp3CBoDHW7LsI9CvyZsg/?imgmax=800)
![WP_20160101_14_37_54_Pro_thumb[1] WP_20160101_14_37_54_Pro_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhhOVbnUvUxdPHgx2eq8mo35NvkL3S0EL1Wa_0fE136nM84z-GNxTB9tRKa_DXcAqtn9TCMU8Cgwe3y2rCA5u5p9yLwUFI-RRlXaKrhZF2dFQ91BfDDA30AvmgEKJLvVBxdYyt0NQ5Asw/?imgmax=800)
![WP_20160101_14_38_34_Pro_thumb[1] WP_20160101_14_38_34_Pro_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgIVuXhvhvhNIOAsAusxS3I5YfO0X1F1dRswnUNZNh9CA0FNg0c7tqdj_NXAGEwFOd64I605N7k5nwDkgZymv5uOEGAj8_iWB-QnzdXdKV7AJlTVJYxCByk5p1xg3exu-58KwUhyphenhyphen5IrNw/?imgmax=800)
![dashboard_thumb[1] dashboard_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi_uBWkhWSRYPpgfCbRxKUGPbP2hkbnRHy1PMO00dwJEXjDeJgMKCibyQaGlXSA18zqd6Fho33qT2dq5uvkl04gshQH5te7V1RE-ZZ608abVMn5cnHu-AS5BFKgETKwCr7QfR4tl0yJDg/?imgmax=800)
![pineap_thumb[2] pineap_thumb[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgjmxwsYjkIp77E0jMFPAxPrEZcBYYM6fJsysEwLgL6OO964f0qwMO8EWM1MKULyAnzEd0R52aLn4FNLhPyyLO5YERtFSC3mHFQrPqb00Z6FOkpPlpDFAJ9xUNtt2iT3azaKKkelhEbLQ/?imgmax=800)
![reporting_thumb[1] reporting_thumb[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjYcuh5p5yoSJSwVpiiTZgc6YoG0yU0nzfh9gu_ixVrgiqbgINSV7YGJMo2a5z7gFwNP7Ll98aHkjB8n2xlThfQYBpDbmXy95PN420DDb8RdhZgp9AspuTp-QSM896CESqL1rA5rpr25A/?imgmax=800)


